Executive Overview
In BFSI environments, remote access infrastructure is expected to perform flawlessly, even during peak load conditions. Digital workspace platforms such as VMware Horizon are built for secure access, but the surrounding architecture determines whether that access remains stable under pressure.
The issue is rarely the virtual desktop platform itself.
The issue is how traffic reaches it.
When Unified Access Gateway nodes are directly exposed to internet traffic without a dedicated traffic governance layer, remote access architectures can become fragile under load. Gateway nodes absorb both session handling and traffic distribution responsibilities, increasing operational risk.
This whitepaper explains how introducing NGINX Plus in front of VMware Unified Access Gateway strengthened load resilience, improved availability, and reduced structural exposure in a BFSI deployment.
Executive Value Snapshot
The Problem
Under high traffic conditions:
- Gateway nodes handled direct internet exposure
- Load distribution lacked centralized control
- Node failure risk directly affected user sessions
- Scaling was reactive rather than structured
The Correction
By introducing a reverse proxy and load balancing layer:
- Traffic was centrally governed
- Backend node health was actively monitored
- The load was intelligently distributed
- Failover became automatic and predictable
Result: Improved stability under load without altering the core VMware Horizon deployment.
- Where Remote Access Fails Under Load
In many BFSI environments, remote access architecture follows this pattern:
Internet → VMware Horizon UAG → Internal Systems
While functional, this structure creates stress points when demand increases.
Under load:
- Individual UAG nodes can experience uneven traffic distribution
- Gateway resources may become constrained
- Node outages impact user access directly
- Scaling becomes operationally complex
The root cause is architectural coupling. Gateway nodes are responsible for secure session management and direct internet exposure simultaneously.
In regulated environments, that concentration of responsibility introduces fragility.
- The Architectural Gap
The deployment required a separation of responsibilities.
Traffic control and application gateway functions should not reside in the same layer.
Without a dedicated traffic management tier:
- Public exposure cannot be effectively abstracted
- Load balancing is limited
- Failover behavior lacks centralized awareness
- Operational stability depends heavily on individual node performance
The architecture needed reinforcement at the edge.
- The Structural Fix
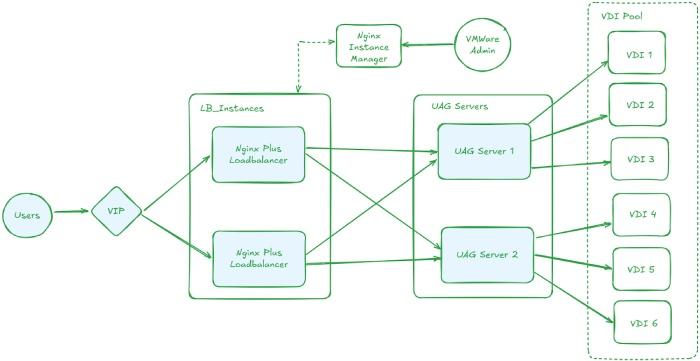
The revised design introduced NGINX Plus as a reverse proxy and load balancer in front of the UAG cluster.
Revised flow:
Internet → NGINX Plus → VMware Horizon UAG Cluster → Internal Systems
This adjustment created a structured entry point for all inbound traffic.
- What Changed Architecturally
4.1 Intelligent Load Distribution
NGINX Plus distributes incoming requests across multiple UAG nodes.
This ensures:
- Balanced resource utilization
- Reduced overload on individual gateways
- Improved performance consistency during traffic spikes
Load resilience became engineered rather than assumed.
4.2 Health-Aware Failover
Continuous backend monitoring enables automatic removal of unhealthy UAG nodes from rotation.
If a node becomes unavailable:
- Traffic is redirected to healthy instances
- User disruption is minimized
- Service continuity is preserved
Availability becomes predictable even under failure scenarios.
4.3 Reduced Exposure Surface
Placing NGINX Plus at the edge introduces a controlled ingress layer.
Instead of directly exposing UAG nodes:
- External traffic terminates at the proxy layer
- Backend systems operate behind controlled routing
- Gateway exposure is minimized
Security posture strengthens without modifying VMware Horizon’s core behavior.
- Design Principles Applied
This architecture reflects three practical principles.
Principle 1: Separate Traffic Governance from Gateway Logic
Application gateways manage sessions.
Traffic governance belongs at the edge.Separating these concerns reduces operational strain and improves scalability.
Principle 2: Engineer for Load, Not Just Functionality
An architecture that works at low traffic volumes may fail under peak demand.
Centralized load distribution ensures stability during stress conditions.
Principle 3: Design for Failure Scenarios
Node failure should not translate to user outage.
Health-aware routing ensures resilience when backend components degrade or fail.
- Operational Impact
The introduction of a dedicated traffic control layer delivered measurable operational improvements:
- Simplified scaling of UAG infrastructure
- Reduced manual intervention during node outages
- Centralized traffic visibility
- Improved reliability under high concurrency
The digital workspace became structurally stable rather than conditionally stable.
- Strategic Outcome
For BFSI institutions, remote access reliability is not optional.
By introducing NGINX Plus in front of VMware Horizon UAG, the deployment achieved:
- Load resilience
- Controlled exposure
- Health-aware routing
- Improved operational predictability
The architecture did not replace existing infrastructure.
It strengthened how traffic reached it.
Conclusion
BFSI remote access architectures fail under load when gateway systems are tasked with both session management and direct internet exposure.
They succeed when traffic governance is separated into a dedicated edge layer.
By introducing NGINX Plus in front of VMware Unified Access Gateway, the environment restored structural stability, enhanced availability, and reduced exposure risks.
In regulated environments, resilience is not a feature.
It is an architectural decision.